The purpose of the cyber awareness challenge is to influence behavior by focusing on actions that authorized users can engage to mitigate threats and. First, they help prevent insider threats by providing leadership with threat information that may help to. Discourage employees from becoming insider threats through training, outreach and. Web to help study cyber awareness for the fiscal year 2023 learn with flashcards, games, and more — for free. Web insider threat programs are intended to:
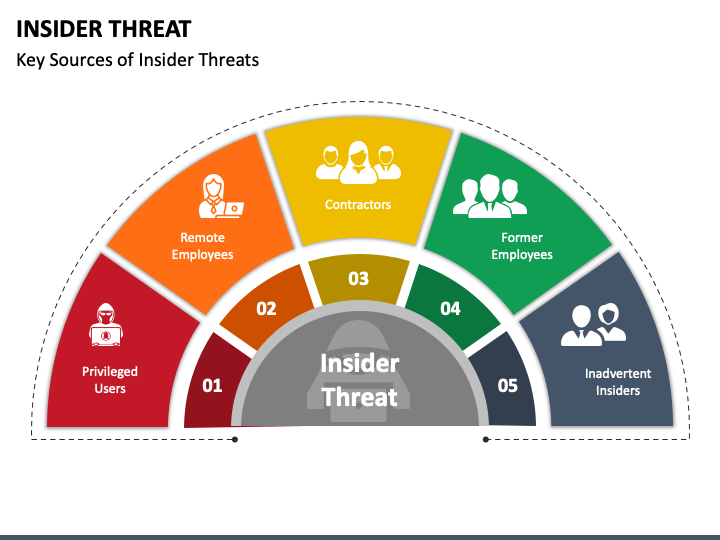
Web an insider threat uses authorized access, wittingly or unwittingly, to harm national security through unauthorized disclosure, data modification, espionage, terrorism, or kinetic. Web scheduled, elearning facilitated by instructors through cdse's online collaborative learning environment. Web this course provides a thorough understanding of how insider threat awareness is an essential component of a comprehensive security program. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Discourage employees from becoming insider threats through training, outreach and.
First, they help prevent insider threats by providing leadership with threat information that may help to. Verified correct answer proactively identify potential threats and formulate holistic mitigation responses. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their authorized access, intentionally or unintentionally, to. Web what functions do insider threat programs came to fulfill? Combating the enemy within, by clive blackwell.
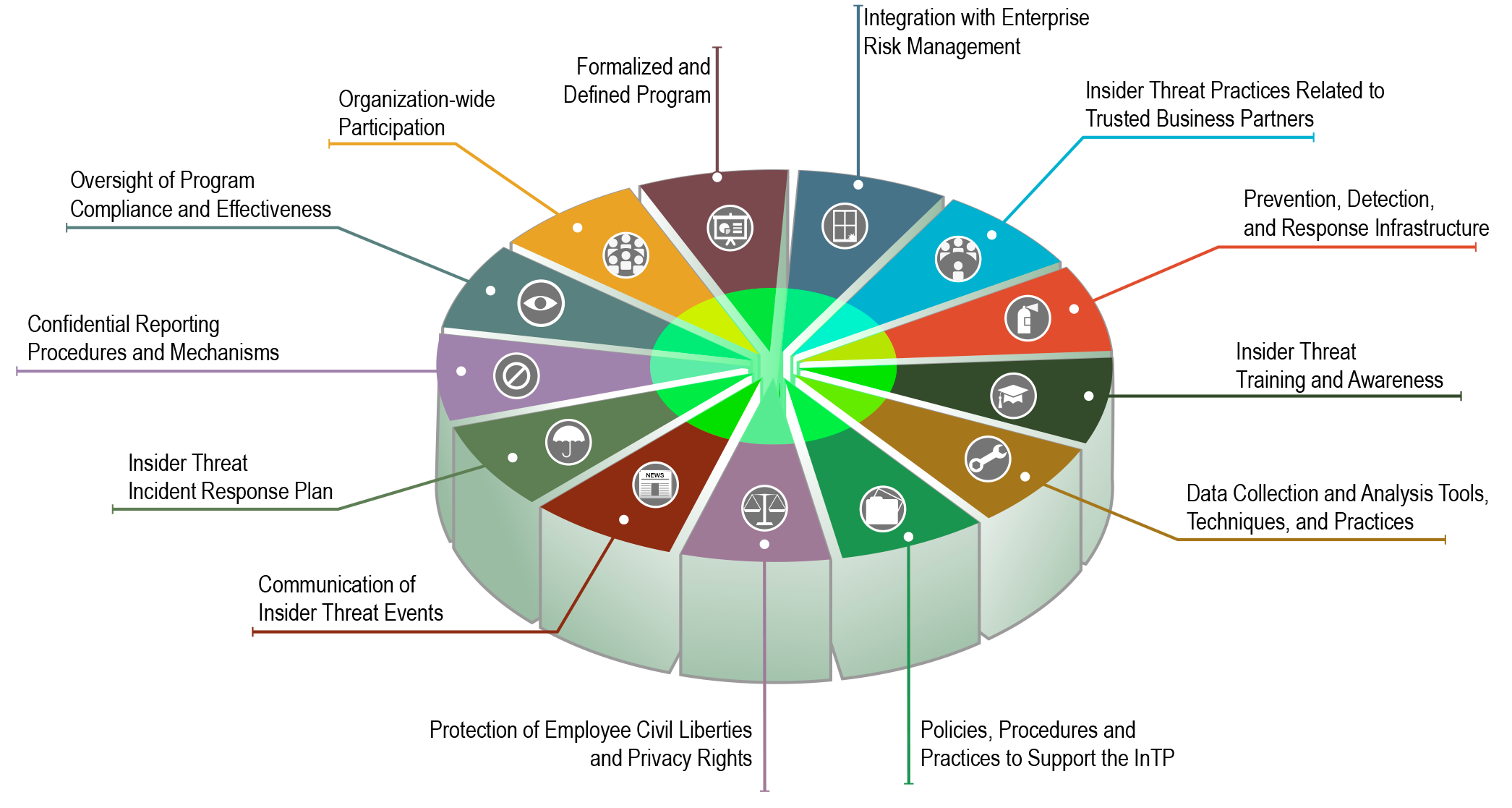
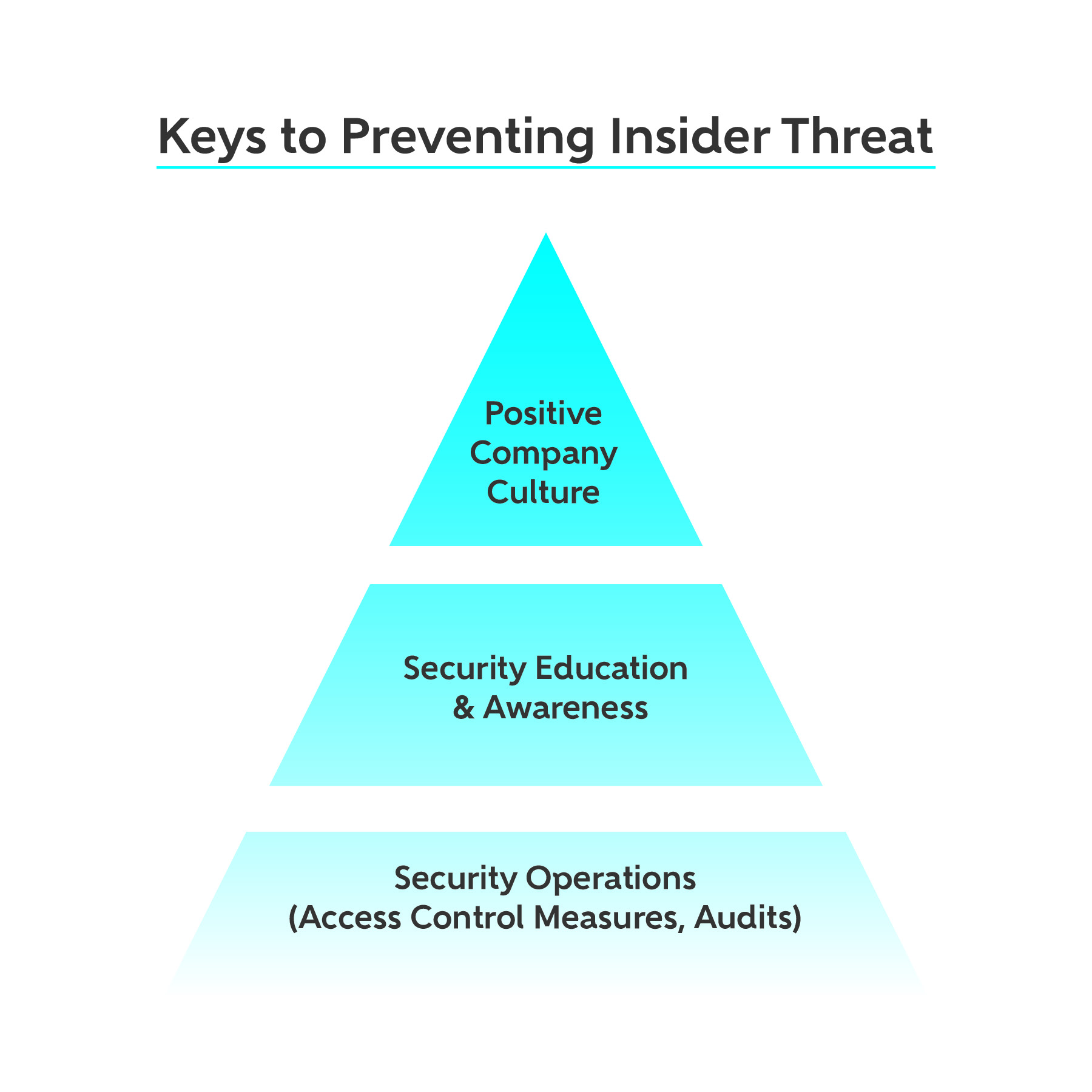
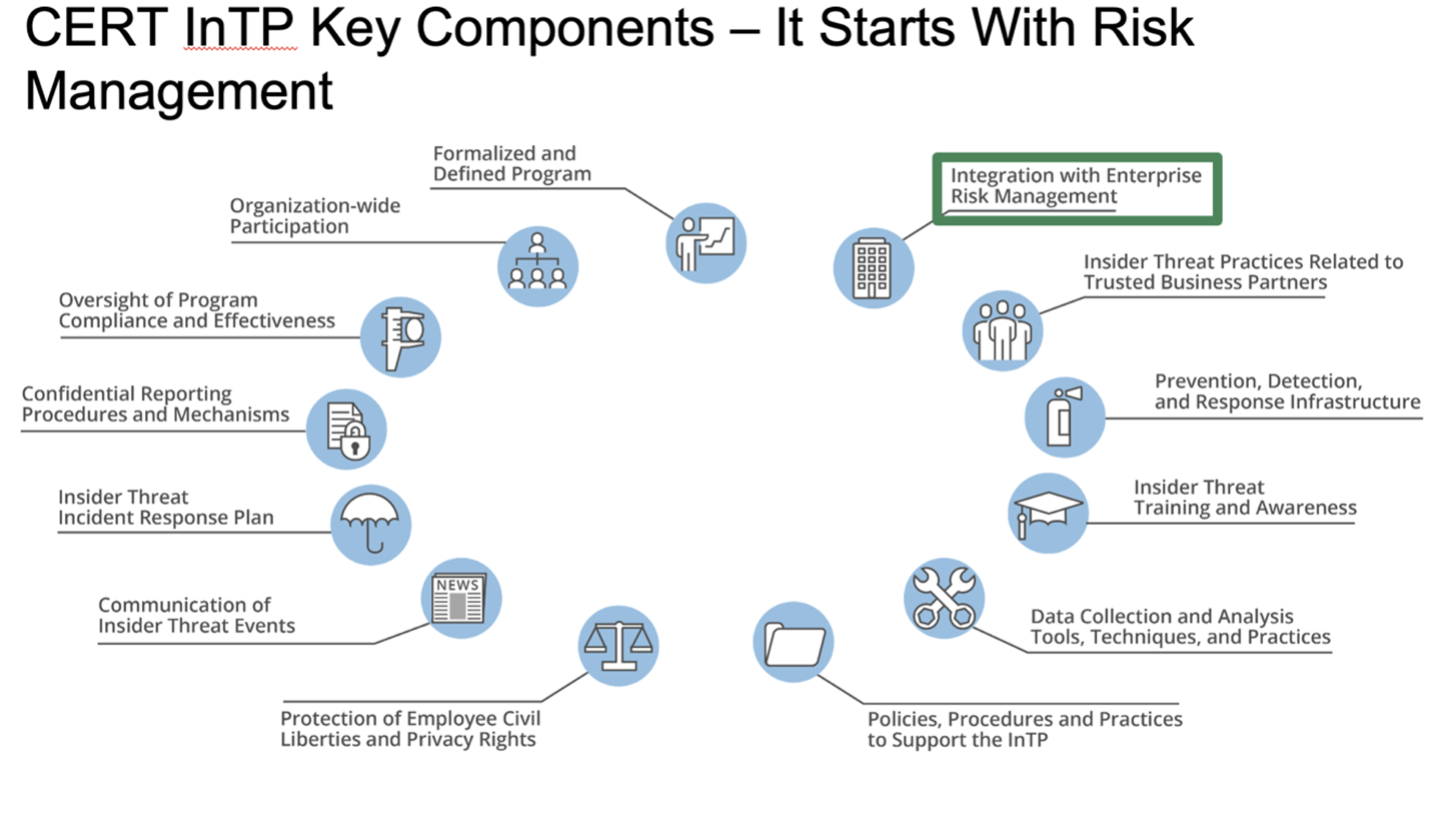
Web insider threat programs fulfill four functions using a holistic approach. Detect insiders who pose a risk to classified information; Web this course provides a thorough understanding of how insider threat awareness is an essential component of a comprehensive security program. Web insider threat mitigation programs need to be able to detect and identify improper or illegal actions, assess threats to determine levels of risk, and implement solutions to manage. Web an insider threat uses authorized access, wittingly or unwittingly, to harm national security through unauthorized disclosure, data modification, espionage, terrorism, or kinetic. • acknowledge that insider threat is real. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their authorized access, intentionally or unintentionally, to. Web to help study cyber awareness for the fiscal year 2023 learn with flashcards, games, and more — for free. Web this fact sheet provides organizations a fundamental overview of insider threats and the key components to building an insider threat mitigation program. Deter cleared employees from becoming insider threats; Combating the enemy within, by clive blackwell. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web my tips for building or enhancing your insider threat program include the following: Web insider threat programs are crucial for preventing security breaches from within an organization by educating employees about cyber threats and vulnerabilities. Web these policies define the purpose of insider threat programs as deterring, detecting, and mitigating insider threats.
Web This Fact Sheet Provides Organizations A Fundamental Overview Of Insider Threats And The Key Components To Building An Insider Threat Mitigation Program.
Web this course provides a thorough understanding of how insider threat awareness is an essential component of a comprehensive security program. • acknowledge that insider threat is real. Verified correct answer proactively identify potential threats and formulate holistic mitigation responses. Insider threat programs fulfill several functions, including identifying and mitigating potential risks.
Insider Threat Programs Are Designed To Deter, Detect, And.
Web scheduled, elearning facilitated by instructors through cdse's online collaborative learning environment. Detect insiders who pose a risk to classified information; Web what function do insider threat programs aim to fulfill? Identify where you have the most.
Combating The Enemy Within, By Clive Blackwell.
Web insider threat mitigation programs need to be able to detect and identify improper or illegal actions, assess threats to determine levels of risk, and implement solutions to manage. Web my tips for building or enhancing your insider threat program include the following: The purpose of the cyber awareness challenge is to influence behavior by focusing on actions that authorized users can engage to mitigate threats and. Web insider threat programs fulfill four functions using a holistic approach.
Web The Insider Threat Mitigation Guide Provides Comprehensive Information To Help Federal, State, Local, Tribal, And Territorial Governments;
Discourage employees from becoming insider threats through training, outreach and. Web an insider threat is anyone with authorized access to the information or things an organization values most, and who uses that access, either wittingly or unwittingly, to. First, they help prevent insider threats by providing leadership with threat information that may help to. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat.